With personal information worth more than credit card details to fraudsters, Emma Herrod ask whether retailers are giving cyber criminals easy access to their customer data.
When asked why he robbed banks, American outlaw Jessie James allegedly replied: “Because that’s where the money is.” That’s no longer strictly true, however, as it’s the credit card and personal details of their customers that many organisations hold that are now of real value to criminals. While the credit cards themselves have only a limited life because a stop can be put on them when they’ve been compromised, the new ‘money’ is the personal data that retailers collect by the bucket load.
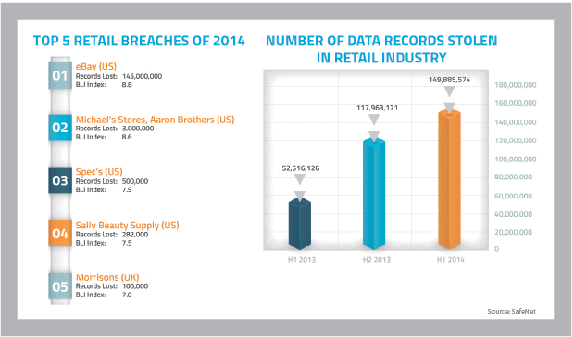
Hackers are adept at accessing this valuable – and vulnerable – data. For example, for 19 days during November and December 2013, hackers accessed the details of around 40 million customers of US retailer Target. The information they captured by hacking into store-based POS terminals included name, credit/debit card number, expiry date and CVV. The company later discovered that the details of up to 70 million shoppers – names, addresses, phone numbers and email addresses – had been illegally accessed.
The Target breach wasn’t caused by a fault with its website: hackers gained access via network credentials stolen following an email malware attack on the firm’s air conditioning service company. What is more worrying is that the breach could have been prevented by Target’s existing security systems if it had heeded warnings, according to an investigation by Bloomberg Businessweek.
NOT THE ONLY TARGET
Target is not alone in being hacked. Domino’s [irdx RDOM] has been held to ransom by cyber criminals threatening to release the details of 600,000 of its customers, while Office reported that its website had been the subject of a security breach resulting in criminal access to shoppers’ accounts and passwords. In the UK alone over the past year, more than 100,000 customer records are known to have been hacked.
Cyber crime is not an issue that’s going to go away; while the number of breaches of UK companies’ secure systems is declining, Andrew Miller, Cyber Security Director at PwC, says they are “becoming more sophisticated and their impact more damaging”. Each breach can cost large organisations between £600,000 and £1.15m, according to the Department for Business Innovation & Skills/PwC 2014 Information Security Breaches Survey.
This found that among large businesses (not just retailers) in the past year:
❚ 55% were attacked by an unauthorised outsider (down from 66% a year ago);
❚ 73% were infected by viruses or malicious software (up from 59%);
❚ 38% were hit by denial of service attacks (similar to the previous year’s 39%);
❚ 24% detected that outsiders had successfully penetrated their network (up from 20%);
❚ 16% knew that outsiders had stolen their intellectual property or confidential data (up from 14%).
New EU data protection regulations will be introduced next year, and the Financial Conduct Authority Regulations, which affect listed companies, contain reporting requirements relating to data and security breaches. “The fines which can be imposed following security breaches are significant and the litigation risk arising out of these incidents, for example, breach of contract claims by customers or claims for negligence, can be substantial,” comments Kim Walker, Technology Partner at law firm Thomas Eggar.
However, these security breaches don’t only hit retailers in the pocket, they also damage their reputation and lose them trade.
It’s not a question of if a company will be hacked but when.
THE GREAT ATTRACTION
Retailers have been busy building big data databases, collecting information about customers, alongside their credit and debit card details, and connecting an ever-increasing number of touchpoints to the internet. “Cyber criminals have increasingly swung their attention to retailers as a target as they look for information on customers,” says TK Keanini, CTO of network security firm Lancope.
They don’t just want credit card data, but anything that can be monetised, either by those behind the attack or whoever they sell the stolen data to.
Andy Heather, VP EMEA at Voltage Security, comments: “The value of personal data continues to be recognised by hackers, who are now attempting to use the data to hold companies to ransom. The theft of financial information (credit card or account information) has a limited lifespan – until the victim changes their account details etc – but it’s not so easy to move house or change your date of birth.
“The personal information that can be obtained has a much broader use and can be used to commit a much wider range of fraud and identity theft, and simply cannot be changed. A single stolen credit card is a worth around $1; if that card information is sold with a full identify profile, that can dramatically increase to up to $500.”
This all means that any large retailer will be a very attractive target, and the risk becomes greater with more information being stored in one place with an increasing number of access channels and access points.
Retail is a very open business, and its POS terminals, wireless networks and accessibility anywhere, anytime make it very vulnerable, explains Heather. “Anything you or I could get access to, a cyber criminal would want to access,” he warns.
It’s also a very dynamic environment, since access points change and are updated along with new channels. Although there are security protocols, retail moves so fast that things sometimes go wrong or updates aren’t completed to the right specification. Hackers will be testing all of these points, all of the time, looking for these vulnerabilities.
All it takes is for one employee to be on holiday or for the team to forget to patch something on time and an access point is created. Even skilled IT staff make security mistakes or miss something when checking their own code. “That’s why independent IT security testing is something retailers should do,” comments Ilia Kolochenko, CEO of information security company High-Tech Bridge.
Paul Hampton, Payment & Crypto management Expert at SafeNet, which tracks UK retail industry breaches via its Breach Level Index, explains that most of these breaches are via digital. Some originate within the company, so employees should have access only to the data they need.
Most security experts agree that it’s not a question of if a company will be hacked but when.
Heather comments that retailers should not focus on the level of due diligence in moving systems and securing end points, but think about making the end information unusable. “At some point, the bad guys will get into your organisation. Is there something you can do to the information to make it unusable or unreadable so that the criminals go elsewhere?” he asks. In the case of the Target hack, the customer data was stored as non-encrypted cleartext.
Unprotected data gives cybercriminals almost all of the information needed to commit fraud. Even throwaway information such as loyalty data or a postcode is at risk and has a value.
Hart believes that if Office had employed format-preserving encryption to protect its data, hackers would have ended up with encrypted information of no use – and therefore no value – to cyber criminals.
PRIDE BEFORE A FALL
The vast majority of hacks aren’t revealed with about 70% of organisations keeping their worst security incidents secret. So what we read or hear about in the news is just the tip of the iceberg. Unfortunately, there will also be many more incidents that will remain undiscovered because companies are not monitoring all the potential access points. Essentially, if you don’t know about it you can’t do anything about it.
It’s not just an issue for large retailers, either. While there are high-profile criminals looking for a big win (and seeking the attention of Interpol and UK Cyber Crime Units), most want to remain invisible. Many are happy to keep a lower profile and pocket £2 each from 1 million customers.
It’s also more complicated for cyber criminals to sell a large database of customer information. Kolochenko believes the recent high-profile attack on eBay, which resulted in many users around the world changing their passwords, was likely to have been targeted specifically.
There’s a co-evolution that takes place with security, explains Keanini. Many people don’t fit a burglar alarm until after they’ve been burgled and the same is true of some retailers: they don’t get on top of security issues until after an attack. “Inevitably, every retailer has to accept the ‘adversary’ as part of doing business,” he says.
Not only does the company need to check its own security across its infrastructure and employees, but it also needs to be aware of every possible access point, from the supply chain to its customers. Any of these are vulnerable to attack and criminals may not target the most obvious ones.
“As one door gets locked and secured another opens as an access point,” comments Heather.
For every breach that’s occurring there are several that haven’t been detected
STANDARDS
There are standards in place and processes that have to be followed to keep certain data secure, such as PCI compliance for credit card data or HIPAA for healthcare data. But are these enough?
In December 2014, PCI DSS 3.0 comes into force in the UK. The PCI Security Standards Council says that it wants this standard to bring about a sea change that will involve a “structured, predictable and continuous” approach to PCI compliance.
The TK Maxx breach and the attack on Target have highlighted the need for a broader, more holistic approach to PCI. Many of these enhanced standards focus on employee education and awareness, eliminating the use of default passwords and the need to write down payment card details, stopping access by phishing scams and ensuring the use of approved encryption methods. This comprehensive compliance ideology also comes with a need for regular systems testing – something that usually involves more time, money and expertise.
However, Keanini believes that standards provide only a base line, and that retailers should be doing more to secure their infrastructure, systems and customers. He comments that standards give a “certain level of fitness but not a place or win at the World Cup. Criminals innovate at a faster rate than standards.”
Currently, only 12% of IT organisations in the UK are completely confident that their endpoints are compliant with the upcoming PCI DSS standard.
Given the increasing number of data breaches and the amount of customer data that retailers hold, in a single place, retailers need to appreciate the true value of what they have and the consequences if it’s stolen.
Retailers can turn things around by having the right operational processes to outmanoeuvre their adversaries, and making it harder for them to infiltrate systems or remain hidden. For example, a large retailer may have hundreds of vulnerabilities but a single adversary has to find only one of them – and remain undetected. “They may try 7 or 10 manoeuvres but all the defender has to do is find them at one of them,” says Keanini.
If retailers treated cyber criminals as if they were as important as their customers’ purchasing data, it would minimise the risk to a point that makes it insignificant.